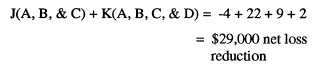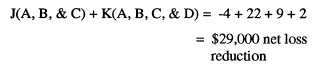be noted. At this point, there exists a matrix of
individual threats and remedial measures with estimates
of loss reductions and costs, and thus an estimate of the
net saving. This is shown graphically in table 4-4.
For each threat (A, B, C, and D), the estimated loss
reduction (column 1), the cost of the remedial measure
(column 2), and the net loss reduction (column 3) are
given in thousands of dollars. By applying remedial
measure J to threat A at a cost of ,000, a loss reduction
of ,000 can be expected (a net saving of
||content||
1,000).
Furthermore, remedial measure J will reduce the threat
B loss by ,000 at no additional cost and the threat C
loss by ,000 at an added cost of only
||content||
,000. Finally,
though, it appears that it would cost more than it would
save to apply J to threat D. Therefore, J would not be
implemented for D. The net loss reduction from J could
be expressed as:
The table indicates that J and K have the same reduction
effect on threat A. Since K costs more than J, it might,
at first glance, be rejected. However,
and
Therefore, while J and K are equally effective on threat
A, K appears to be more effective than J on the other
threats. Further checking shows their combined use
results in the greatest overall net loss reduction.
By going through the process just described, using
preliminary estimates for cost and loss reduction, you
can test various combinations of remedial measures,
and thus identify the subset of remedial measures that
appears to be the most effective. At this point, review
the estimates and refine them as necessary to ensure
compliance with higher authority security instructions.
If all the preceding procedures are followed, the
following factors will be established and documented:
l The significant threats and their probabilities of
occurrence;
l The critical tasks and the loss of potential related
to each threat on an annual basis;
l A list of remedial measures that will yield the
greatest net reduction in losses, together with
their annual cost.
With this information at hand, AIS upper
management can move ahead with implementing the
AIS security program. Since the analysis of remedial
measures will have identified those with the greatest
impact, relative priorities for implementation can also
be established.
AIS DISASTER PROTECTION
Fires, floods, windstorms, and earthquakes all tend
to have the same basic effects on AIS operations. They
cause the physical destruction of the facility and its
contents and interrupt normal operations. They also
represent a threat to the life and safety of the AIS staff.
To illustrate the effects of the physical destruction of a
facility, we have selected fire safety. Other causes of
disasters include the loss of support utilities and
breaches of AIS facility physical security.
FIRE SAFETY
Experience over the last two decades demonstrates
the sensitivity of AIS facilities to fire damage resulting
in disruption of operations. A number of major losses
Table 4-4.—Threat Matrix Table
4-18