particular attack or event to occur?” Remember, the
successful attack or adverse event results from a
particular threat exploiting a particular vulnerability. It
is very specific reasoning. The greater the value of the
AIS asset and the more likely the successfid attack or
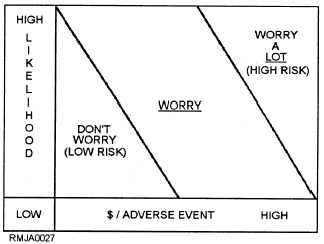
adverse event, the greater the risk. Figure 4-3 shows
this risk analysis concept. Risks are usually expressed
in terms of dollars per year, the annual loss expectancy.
Countermeasures
Once the threats and vulnerabilities are known and
the likelihood and risk of a successful attack or an
adverse event are determined, a plan is developed to set
up countermeasures (controls) to lessen or eliminate the
vulnerabilities. If you have a countermeasure, you have
a protected vulnerability. If you have an unprotected
vulnerability, you do not have a countermeasure. Some
countermeasures help us prevent adverse events,
whereas others detect adverse events.
We have
measures to minimize the effects of successful attacks
or adverse events. We also have measures, called
contingency plans, to recover from a successful attack
or an adverse event. Figure 4-4 gives an example of
each type of security measure strategy as it relates to
fire loss. Figure 4-5 shows threats, vulnerabilities, and
countermeasures to our assets.
Another way to categorize countermeasures is by
type: physical, technical, administrative, and
managerial (figure 4-6).
PHYSICAL CONTROLS.— We usually think of
physical control first. They include the locked
computer room door, physical layout, fire
extinguishers, access barriers, air conditioners,
moisture detectors, and alarms.
Figure 4-3.—AIS security risk analysis.
4-4
TECHNICAL CONTROLS.— Technical con-
trols are embedded in hardware, software, and
telecommunications equipment. They are diagnostic
circuitry, component redundancies, and memory
protect features. They are controls built into the
operating system. They include log-on IDs and
passwords to enable only authorized users access to the
computer system. They are accounting routines,
encryption coding, and audit trails.
ADMINISTRATIVE CONTROLS.— Ad-
ministrative controls concern people and procedures.
They include who is authorized to do what, methods to
keep track of who enters a sensitive area, who receives
a delivery, and who requests a sensitive report. The
operating procedures you follow will sometimes
include security requirements. You are responsible for
adhering to the procedures to ensure AIS requirements
are met.
MANAGERIAL CONTROLS.— Managerial
controls tie everything together. They concern
planning and evaluation. They include audits to review
the effectiveness and efficiency of the countermeasures.
They check to make sure that the measures are actually
in place, being followed, and working. Problems found
require replanning and reevaluation to see that
corrections are made.
RISK MANAGEMENT
Risk management involves assessing the risks,
determining loss potential estimates, and selecting
countermeasures appropriate to prevent, detect,
minimize, and recover from successful attacks and
adverse events. Management selects the
countermeasures, making sure that the cost of the
measure is less than the cost of the risk. The trick is to
select the countermeasure that will result in the lowest
total cost while taking all reasonable measures to
protect our AIS assets.
Keep in mind that the presence of a vulnerability
does not in itself cause harm. A vulnerability is merely
a condition or set of conditions that may allow the
computer system or AIS activity to be harmed by an
attack or event. Also, keep in mind that an attack made
does not necessarily mean it will succeed. The degree
of success depends on the vulnerability of the system or
activity and the effectiveness of existing
countermeasures. Countermeasures may be any action,
device, procedure, technique, or other measure that
reduces the vulnerability of an AIS activity or computer
system to the realization of a threat.