Their value can usually be stated in dollar terms. It costs
money to repair or replace hardware. It costs money to
reprogram and redocument. It costs money to retrain
personnel. Unauthorized access costs money. Service
delays cost money.
AIS Assets
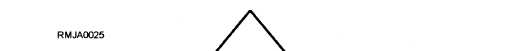
Our AIS assets (figure 4-1) include the facilities,
hardware, software, data, supplies, documentation,
people and procedures. These assets combine to
provide service. Service is computer time,
telecommunications, data storage, user support,
application system development, and operation.
Service must be available to those authorized to receive
it when they request it. Information is at the top of the
triangle. It is the ultimate AIS asset. Information is the
reason the rest exists.
Threats
Threats are things that can destroy your assets
(figure 4-2). Easy to recognize, threats come in two
basic forms:
people and environmental changes.
People are a threat because they sometimes do
unexpected things, make mistakes, or misuse resources,
steal, subvert, and sabotage (deliberate threats). Some
of us even smoke and spill soft drinks in computer
rooms. Environmental threats are things like heat,
humidity, explosions, dust, dirt, power peaks, power
failures; and natural disasters like fire, floods,
hurricanes, thunderstorms, and earthquakes. Hardware
failures and compromising emanations are also threats.
Another term associated with threats is their probability
of occurrence. What is the likelihood that something
will happen? Probabilities are measured in time—once
a pico second, once a memory cycle, once a fiscal year,
once a century.
Vulnerability
Threats cannot reach an AIS asset without the aid
and assistance of a vulnerability. Vulnerabilities are the
holes threats sneak through or weaknesses they exploit.
Vulnerabilities are caused by lack of AIS security
planning, poor management, disorganization, disorder,
inadequate or improper procedures, open data and open
door policies, undocumented software, unaware or
unconcerned personnel. You can help limit the
vulnerabilities by following established AIS security.
policies and procedures.
Successful Attacks and Adverse Events
Successful attacks and adverse events result from a
combination of threats, vulnerabilities, and AIS assets.
When a threat takes advantage of a vulnerability and
does harm to your AIS assets, a successful attack or
adverse event has occurred. Successful attacks and
adverse events may be roughly grouped as losses or
abuses. You can lose hardware, software, and data.
You can lose documentation and supplies. You can lose
key staff personnel. Losses often result in denial of
service, preventing access to information when it is
Figure 4-1.—AIS assets.
4-2