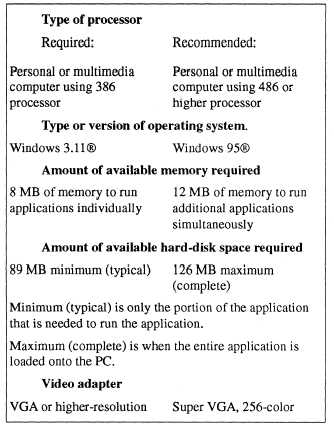
software. You will normally find this information on
the side of the box and sometimes even on the back of
the box the software comes in. The following
requirements and recommendations will normally be
listed:
Any other system/hardware requirements that may
be needed will also be listed. As an example, these
requirements might include: one CD-ROM drive;
microphone, for voice annotation feature; a mouse or
compatible pointing device; 2400 or higher baud
modem (9600 baud modem recommended);
headphones or speakers; and type of messaging
software required to use e-mail; etc.
Once you have determined all of the above
information, you will need to determine whether it will
be run on a network as shared. Before you install the
software, you need to read the installation instructions
that come with the software application in their entirety.
It is strongly suggested that you read a file normally
called the “READ. ME” file, because that is where you
will find the most up-to-date information (changes) that
have been made to the application.
1-8
SOFTWARE TESTING
Once the software is installed on the network, it
must be tested. The reason for the testing is to make sure
that all aspects of the program work. There are two
avenues for testing the software: an independent testing
company, and end-users.
The advantage of an independent testing company
is that it will use a more comprehensive and systematic
testing method. Testing aimed at the generic network
user is the disadvantage of the testing company.
Using end-users has both advantages and
disadvantages when it comes to testing the software. An
advantage is that the end-users will test all facets of the
software. A disadvantage is the haphazard methods of
most end-users when it comes to testing the software.
SYSTEM RESTORATION
The network is the most error-prone of the system
components. Usually, multiple vendors are involved,
and too few qualified personnel are available to support
all the implemented networks. Due to these inherent
problems with the network, system degradation is a part
of operation, and getting the system back into normal
operation is of great importance.
Three primary methods are used to provide service
restoration after system degradation. They are as
follows:
l Redundancy. Redundancy refers to duplicate
hardware and network facility segments that are
available at all times. If the primary path fails, a
secondary path can continue network operation.
l Rerouting. Rerouting is the transmission of
information along alternative paths. The end-to-end
transmission initially required is still obtained.
l Reconfiguration. Reconfiguration is the
manual or automatic reconfiguration of equipment
and/or lines to achieve the original end-to-end
connections. Reconfiguration may be the most costly
method in time because it requires knowledgeable
personnel and the appropriate switching of equipment.
These three modes of operation are short-term
solutions meant to keep information moving. A better
solution is to correct the degraded or failed circuit
and/or equipment so normal operation is restored.