Token Passing
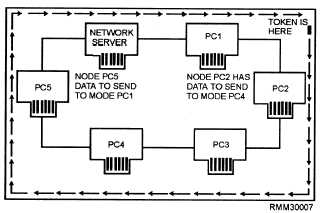
Token passing is an orderly access method (figure
1-7). Each workstation passes on the opportunity to
transmit to its closest neighbor, until a station is found
with a message to send. This permission to transmit is
called a token. When a workstation with data to send is
handed a token, part of the token is changed, indicating
it is carrying a message, and then data is transmitted
with the token. The token is then passed around the
network, and every station checks to see if the message
is intended for them. The receiving station copies the
message from the token but then passes the unchanged
token along the network. When the transmitting station
receives the same token, it knows the message has been
passed around the network. The transmitting station
erases the message and puts the empty token back into
circulation on the network. The amount of information
that may be transmitted during possession of the token
is limited so that all workstations can share the cable
equally.
Network Standards
These access methods (CSMA/CD, CSMA/CA,
and token passing) with their transmission medium
(twisted-pair wire, coaxial cable, or fiber optic cable),
are just one of several aspects (or levels) of an entire
LAN structure. The topologies and network access
methods just presented only establish a way to connect
workstations or nodes together and how to pass along
packets of data. These packets of data may be
programs, data, system or personal messages, and so on.
Above this hardware/software level are a number of
other levels that are just as important in a LAN’s design.
These are the levels that define how the LAN system
manages its resources, how a user like yourself is able to
log onto another node’s hard disk, how a common laser
Figure 1-7.—A ring network using the token passing access
method.
printer is used by all nodes, how one file is passed
among many users, and so on. If order and discipline
are to be maintained on the network, standards or
protocols must be established and adhered to. This
allows the LAN to function in an efficient and effective
manner.
Over the past few years, a number of network
standards or protocols have been developed by the
International Standards Organization (ISO). They
provide some level of uniformity among computer
manufacturers and network vendors. ISO is one of
several governing organizations in this field that has
developed a series of protocols (rules to live by) to
ensure compatibility for the many different vendors
who design network hardware and software products.
IS0 has defined a seven-layer architecture. These seven
layers of standards, shown in figure 1-8, define a
generalized architecture called the Reference Model of
open Systems Interconnection. It is also known as
the OSI reference model or OSI model. The primary
purpose of the OSI model is to provide a basis for
coordinating the development of standards that relate to
the flexible interconnection of incompatible systems
using data communications facilities.
The OSI model does NOT define any one vendor’s
particular network software as such, nor does it define
detailed standards for any given software. It simply
defines the broad categories of functions that each of the
seven layers should perform. The OSI model can
include different sets of standards at each layer that are
appropriate for given situations. For example, in a very
simple data communications system, one that uses a
simple point-to-point link, the software at the higher-
Figure 1-8.—The OSI model showing the seven software
layers.
1-13